Foreword from the First Edition
Acknowledgments
Introduction
Abbreviations
Part I: Fundamentals
Chapter 1: Encryption
Chapter 2: Randomness
Chapter 3: Cryptographic Security
Part II: Symmetric Crypto
Chapter 4: Block Ciphers
Chapter 5: Stream Ciphers
Chapter 6: Hash Functions
Chapter 7: Keyed Hashing
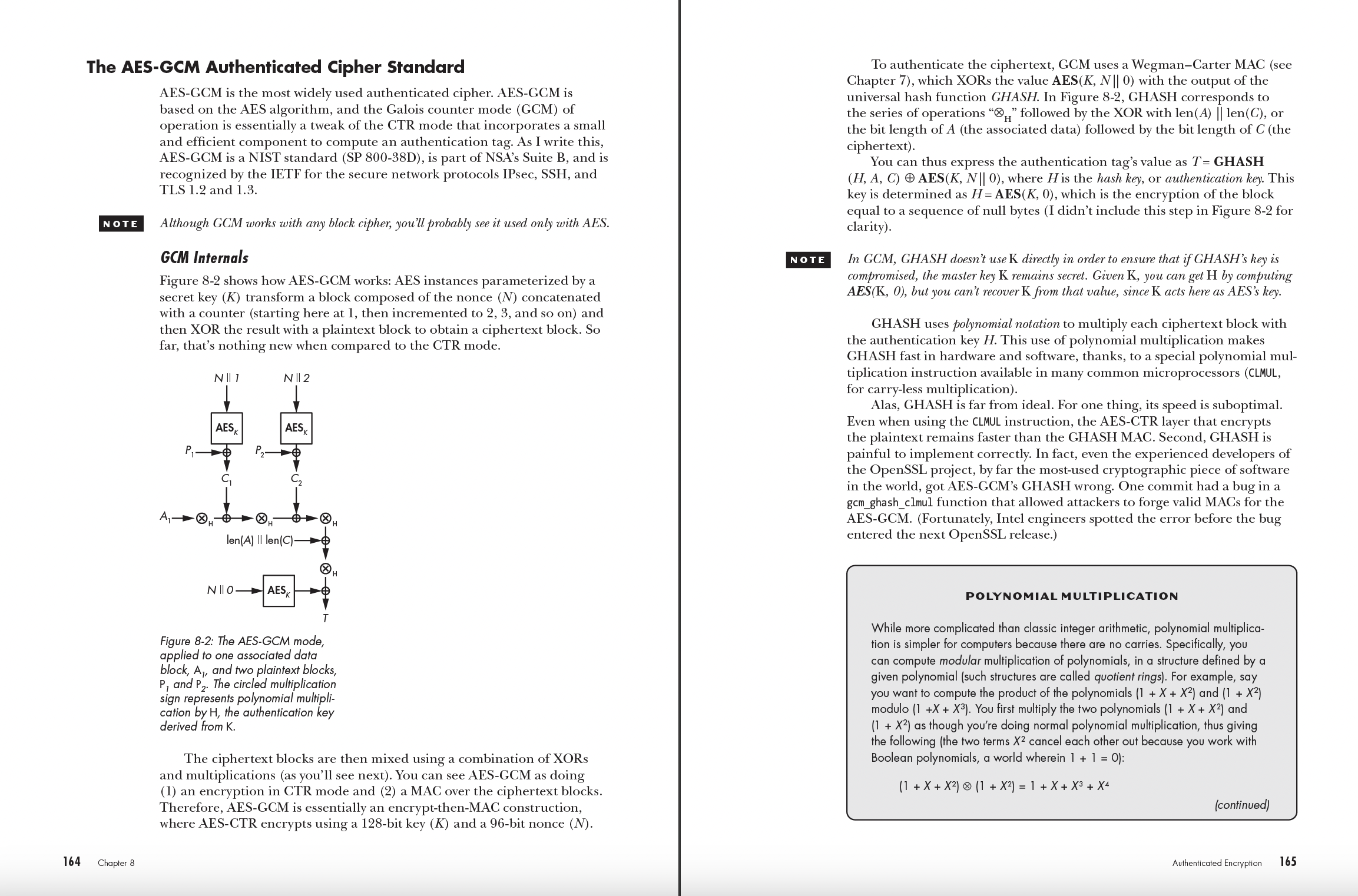
Chapter 8: Authenticated Encryption
Part III: Asymmetric Crypto
Chapter 9: Hard Problems
Chapter 10: RSA
Chapter 11: Diffie–Hellman
Chapter 12: Elliptic Curves
Part IV: Applications
Chapter 13: TLS 255
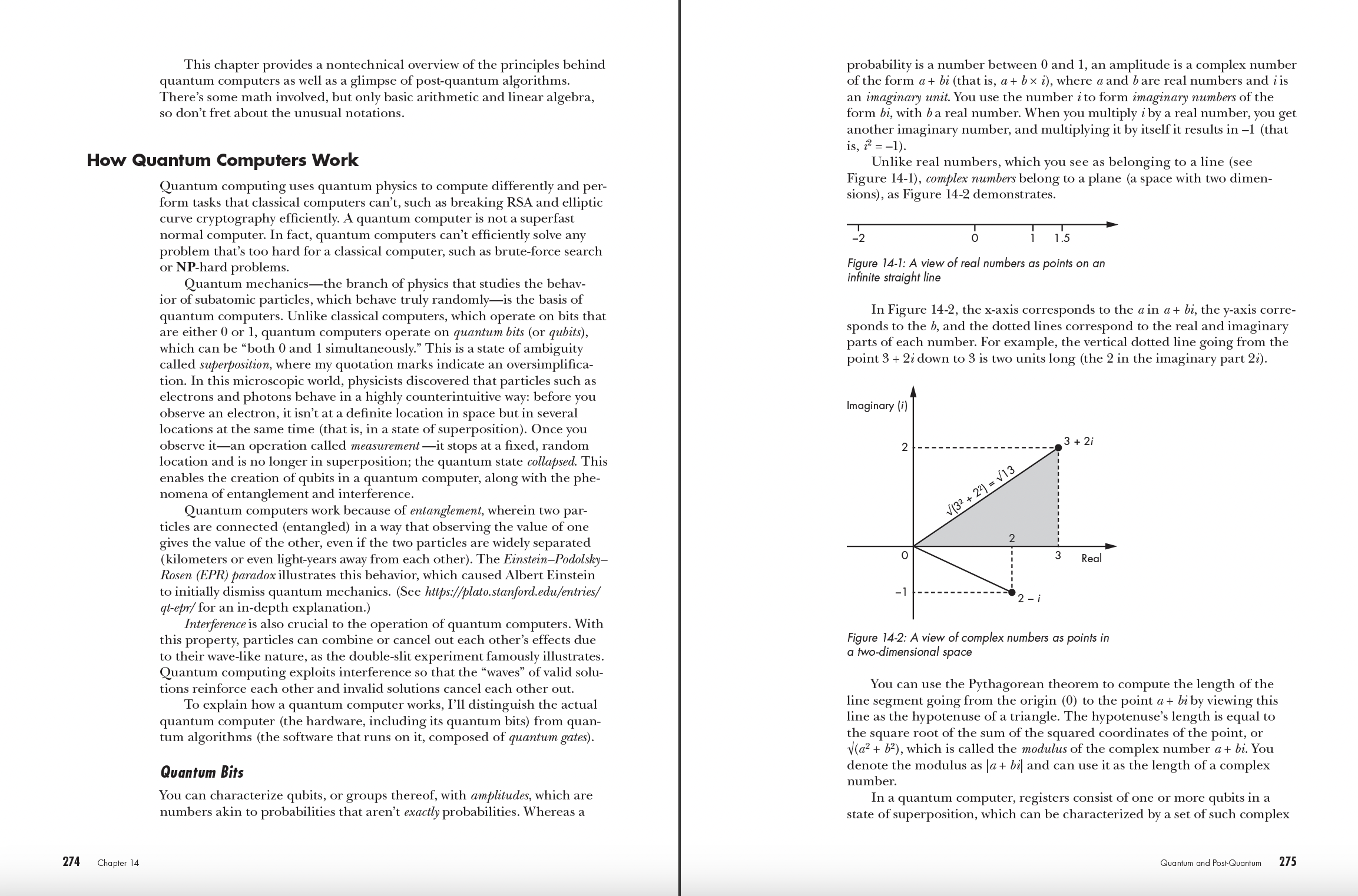
Chapter 14: Quantum and Post-Quantum
Chapter 15: Cryptocurrency Cryptography
Index
Serious Cryptography, 2nd Edition
Download Chapter 2: Randomness
Look Inside!


This thoroughly revised and updated edition of the bestselling introduction to modern cryptography breaks down fundamental mathematical concepts without shying away from meaty discussions of how they work. In this practical guide, you’ll gain immeasurable insight into topics like authenticated encryption, secure randomness, hash functions, block ciphers, and public-key techniques such as RSA and elliptic curve cryptography.
You’ll find coverage of topics like:
- The basics of computational security, attacker models, and forward secrecy
- The strengths and limitations of the TLS protocol behind HTTPS secure websites
- Quantum computation and post-quantum cryptography
- How algorithms like AES, ECDSA, Ed25519, Salsa20, and SHA-3 work
- Advanced techniques like multisignatures, threshold signing, and zero-knowledge proofs
Each chapter includes a discussion of common implementation mistakes using real-world examples and details what could go wrong and how to avoid these pitfalls. And, true to form, you’ll get just enough math to show you how the algorithms work so that you can understand what makes a particular solution effective—and how they break.
NEW TO THIS EDITION: This second edition has been thoroughly updated to reflect the latest developments in cryptography. You’ll also find a completely new chapter covering the cryptographic protocols in cryptocurrency and blockchain systems.
Whether you’re a seasoned practitioner or a beginner looking to dive into the field, Serious Cryptography will demystify this often intimidating topic. You’ll grow to understand modern encryption and its applications so that you can make better decisions about what to implement, when, and how.
"Fills [the need for an accessible and readable resource on cryptography], taking the reader on a journey through different cryptographic tools and how to use them, as well as the important 'what can go wrong' sections that fill the book. . . Serious Cryptography is an enjoyable introduction to the field, and one that comes highly recommended."
—Yehuda Lindell, Head of Cryptography at Coinbase
“A properly serious introduction; it describes the essential concepts in a clear and concise prose. It does not aim at vacuous entertainment of the reader, but at imparting knowledge. This is the kind of ‘first book’ that you’d keep referring to because it has the right structure on which one can build a thorough understanding of cryptography.”
—Thomas Pornin, Technical Vice President, NCC Group
“Like having a wise friend explain all of cryptography's mysteries without making your head spin. The book stands out for its practical approach, which provides real-world applications and insights. It is considered mandatory reading for security engineers undergoing onboarding within my team, providing an essential foundation for their professional development.”
—Anastasiia Voitova, Head of security engineering at Cossack Labs
Reviews from the First Edition:
“A superb introduction to modern encryption and cryptography. For those looking to quickly get up to speed on the topics, this makes for an excellent go-to guide.”
—Ben Rothke, RSA Conference
“For those who really want to understand how cryptography works, and who need to use it in practice, I thoroughly recommend Serious Cryptography.”
—Martijn Grooten, Virus Bulletin
“Aumasson successfully ensures that the reader has a strong understanding of cryptography’s core ideas... Serious Cryptography is a must read for anyone wanting to enter cryptographic engineering.”
—Infosecurity Magazine
“Each chapter not only explains concepts and key implementation details, but also highlights possible pitfalls, common mistakes, and finishes with a list of recommended materials.”
—Artificial Truth
“Impressive in its breadth...the state of the art in applied cryptography is distilled here in a mere 282 pages.”
—Federico Lucifredi, The Hub
"For those wanting to go beyond the basics of cryptography in the blockchain, 'Serious Cryptography' by Jean-Philippe Aumasson is an invaluable resource."
—Halborn Security
View the latest errata

